You know EEM from Cisco and you want something similar on PAN-OS.
It is possible (at least for simple actions).
I wrote a KB article about how to be alerted when there is a version mismatch between HA pairs. That show a way to : perform an action (send an alarm) based on an event (system logs about the version mismatch).
In this post, I will uncover a way to perform some actions directly on PAN-OS based an event.
Note : the event need to be logged on a forwardable logs (one of the logs accessible on the Monitor tab).
We cannot prepare event for systems logs on mp-logs for instance.
On PAN-OS, in the log settings, we can define as destination :
- Panorama/CDL
- SYSLOG servers
- EMAIL server
- SNMP Traps
- HTTP server
We cannot customize what is send to Panorama/CDL, but we can customize the SYSLOG/EMAIL/SNMP Traps/HTTP requests generated when a log generated (so by definition, when there is an event).
Let's focus on the HTTP request possibilities.
We can for instance send the log to a twitter account for instance or ... we can take advantage of the PAN-OS XML API interface.
So, events + HTTP server + XML API on the firewall = Event-driven actions
So how do we do that?
step 1 : find the log, you will use. The log need to be relevant and unique for the event (don't select a log which come every day, unless it is your wish)
step 2 : get the API key
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-panorama-api/get-started-with-the-pan-os-xml-api/get-your-api-key.html
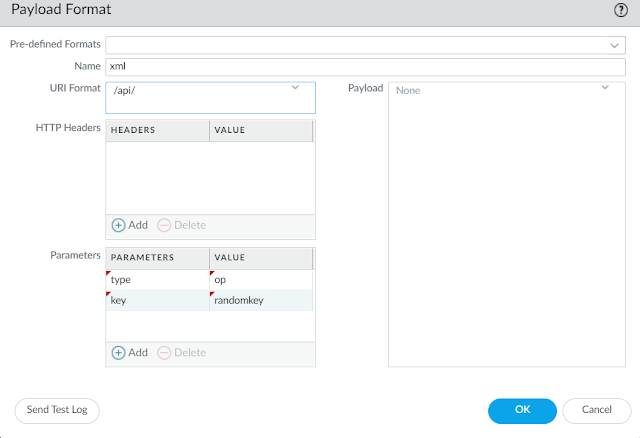
step 3 : create the HTTP server profile.
In the picture above, I created the profile test. You notice the IP address is 127.0.0.1 (the firewall itself) and the protocol used is HTTP and not HTTPS. As the request will not leave the firewall, it is not an issue. And finally, it is a GET request being sent.

No comments:
Post a Comment